Have you heard of quantum computers? These advanced machines are making waves in the tech world, but for all the wrong reasons. It turns out that the loud noises emitted by these powerful devices could actually pose a serious threat to our cyber security.
In a recent study, a team of researchers from the Massachusetts Institute of Technology (MIT) found that the noise produced by quantum hardware could potentially crack the 2048-bit RSA encryption in just seven days. This may sound like a long time in the fast-paced tech world, but when it comes to encryption, that’s lightning fast.
But how does this noisy hardware pose such a serious threat? Well, to put it simply, RSA is a type of encryption that is commonly used to protect sensitive data, such as online transactions and private communications. Its security relies on the fact that it is nearly impossible to factor large numbers into their original prime numbers, making it difficult for hackers to break the code.
Quantum computing has advanced significantly, with new breakthroughs raising concerns about the security of widely used encryption systems. Researchers suggest that quantum computers could soon reach the power necessary to break encryption methods like RSA, which currently protect sensitive digital information.
This progress has sparked discussions about how businesses and governments can prepare for a future where traditional cryptographic methods may no longer be secure. Developing post-quantum security solutions is now a pressing priority as organizations seek to safeguard data against the potential risks posed by quantum computing advancements.
Key Takeaways
- Quantum computing progress challenges current encryption methods.
- Organizations must prioritize post-quantum security solutions.
- The timeline for quantum threats requires urgent preparation.
Google’s Quantum Leap Could Revolutionize Encryption—Q-Day Is Approaching
Confident Investment Decisions Begin with Insight
Quantum computing is rapidly advancing, with a recent breakthrough from Google significantly lowering the threshold for cracking RSA-2048 encryption. This type of encryption is one of the pillars of cybersecurity, safeguarding financial, governmental, and personal data worldwide. Previously, it was believed that breaking this encryption would require at least 20 million qubits. Google’s new findings suggest it could now be achieved with fewer than one million qubits, cutting the required computational resources by 95%.
Although today’s quantum computers lack the capacity to execute such a feat, advancements in quantum technology are narrowing this gap. Achieving a breakthrough would involve sustained quantum operations over several days, supported by exceptional error correction and near-perfect hardware precision. If realized, these capabilities could make quantum supremacy a reality far sooner than expected.
Quick Facts:
- RSA-2048 encryption now deemed vulnerable with fewer qubits than once thought.
- Breakthrough hinges on key quantum properties like superposition and entanglement.
- Adoption of advanced algorithms, such as Shor’s Algorithm, increases decryption risks.
This revelation highlights the urgency for organizations to explore post-quantum cryptography methods and re-evaluate data protection strategies. Reducing dependence on classical computing could help prepare for emerging cybersecurity challenges brought about by quantum computational power.
Why Encryption Concerns Matter to the Market
Quantum computing breakthroughs threaten the security of RSA encryption, whose key length is crucial for protecting sensitive data. If cracked, it could shake investor confidence in digital platforms such as banking, fintech, and brokerage firms. Cybercriminals are already adopting a “harvest now, decrypt later” strategy, targeting encrypted data that could eventually be exposed. Governments, including the U.S. and China, recognize this as a growing issue, motivating the shift to post-quantum cryptography (PQC). Early preparedness by these firms is vital to safeguarding data against future risks. Failing to act might lead to severe consequences for financial systems and digital trust.
Who Benefits from Strengthening Security Against Quantum Threats?
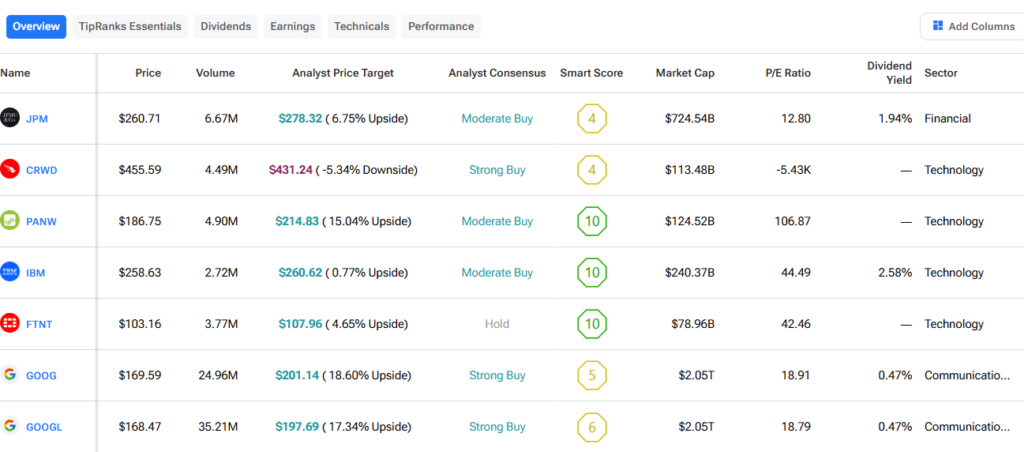
The shift toward post-quantum cryptography has created opportunities for certain organizations to thrive. Cybersecurity companies specializing in quantum-resistant algorithms and advanced architectures, such as zero-trust models, are well-positioned for growth. Firms like Palo Alto Networks, CrowdStrike, and Fortinet are expected to experience increased demand as governments and industries update their defenses to handle the potential risks posed by quantum computing.
Financial institutions stand to gain as well, especially those that have proactively prepared. Banks like JPMorgan, for example, have already started transitioning toward quantum-safe encryption. This forward-thinking approach not only strengthens their security but also serves as a competitive advantage, demonstrating resilience in the face of emerging threats.
On the technology front, companies working on quantum hardware have seen their goals shift from distant aspirations to tangible engineering challenges. Businesses like IBM, Quantinuum, and PsiQuantum have an opportunity to achieve significant breakthroughs if they can commercialize systems with millions of qubits. Success here could usher in a new era of quantum cryptography and other technologies that strengthen encryption methods.
However, not everyone benefits from this transformation. Legacy systems reliant on classical encryption, such as asymmetric encryption or elliptic curve cryptography, may face steep challenges. Cryptocurrencies, many of which depend on traditional public-key algorithms, are particularly vulnerable. Without a shift to post-quantum encryption, some digital currencies could face obsolescence, highlighting the urgent need for adaptation across industries.
The Countdown Continues
Quantum computing presents both promise and risk, especially when it intersects with encryption. Current data security methods face challenges due to the growing risks posed by advanced quantum processors. One pressing threat is the concept of store now, decrypt later, where sensitive information is collected today with the expectation that future quantum computers will ultimately decipher it.
Quantum technology, despite its promise, often struggles with high error rates, an obstacle slowing practical implementation. However, recent breakthroughs suggest the timeline for quantum dominance may be shorter than anticipated. This possibility has sparked urgency among companies to adapt their infrastructure to be quantum-resilient.
Communications and financial systems, deeply reliant on encryption protocols, are likely to experience significant disruptions if security measures aren’t updated promptly. Organizations involved in the quantum future race are investing in strategies to replace vulnerable cryptographic systems ahead of deadlines suggested by experts. Bold initiatives and preparation are becoming essential to safeguard sensitive information from potential breaches.
Frequently Asked Questions
What is ‘Quantum Threat Day’ in quantum computing?
‘Quantum Threat Day,’ sometimes called Q-Day, refers to the moment when quantum computers become powerful enough to break widely-used encryption methods. This marks a significant challenge for the security of digital communications and stored data.
How might quantum computing disrupt current encryption practices?
Quantum computers are predicted to be capable of solving mathematical problems that traditional computers cannot handle efficiently. This includes breaking encryption systems like RSA, which are critical for securing emails, financial transactions, and sensitive digital information.
When could quantum computers start compromising encryption?
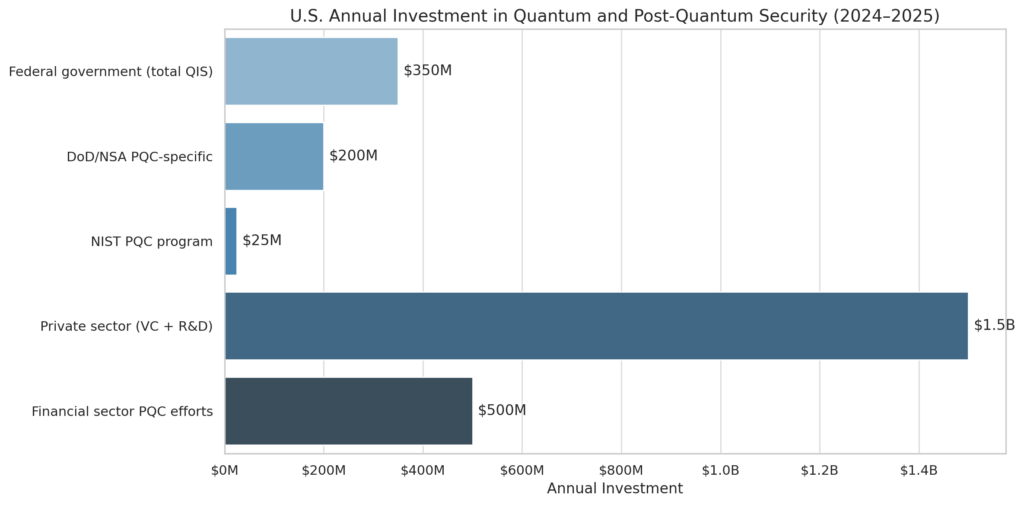
Estimates suggest advancements in quantum technology could enable this within several years. Recent progress by Google Quantum AI indicates that breaking encryption protocols such as RSA-2048 might require fewer resources and less time than previously anticipated. Learn more about the research at Google Research’s findings.
How is cryptocurrency vulnerable to quantum computing?
Cryptocurrencies, including Bitcoin, rely on cryptographic techniques like elliptic curve encryption to secure transactions. If quantum computers become capable of breaking these algorithms, attackers could potentially access private keys, undermining the security and trust in these decentralized systems. Find more context about this issue at Wired’s quantum analysis.
What strategies are being explored to address quantum threats to encryption?
Governments, research institutions, and technology companies are investigating solutions like quantum-resistant encryption. These systems employ algorithms designed to withstand the computational capabilities of quantum machines.
What progress has been made in developing encryption that resists quantum computers?
Work is ongoing to ensure encryption remains future-proof. For example, researchers are creating algorithms believed to be safe against quantum attacks. These innovations represent steps toward safeguarding critical data in the post-quantum era.